Editor’s note: This article was updated in April 2023.
For all its sophistication, the Internet age has brought on a digital plague of security breaches. The steady drumbeat of data and identity thefts spawned a new movement and a modern mantra that’s even been the subject of a U.S. presidential mandate — zero trust. So,
Zero Trust Defined
Zero trust is a security strategy and framework for verifying every user, device, application and transaction on a network in the belief that no user or process should be trusted.
That definition comes from the NSTAC report, a 56-page document on zero trust compiled in 2021 by the U.S. National Security Telecommunications Advisory Committee, a group that included dozens of security experts led by a former AT&T CEO.
In an interview, John Kindervag, the former Forrester Research analyst who created the term, noted that he defines it this way in his Zero Trust Dictionary: Zero trust is a strategic initiative that helps prevent data breaches by eliminating digital trust in a way that can be deployed using off-the-shelf technologies that will improve over time.
What Are the Basic Tenets of Zero Trust?
In his 2010 report that coined the term, Kindervag laid out three basic tenets of zero trust. Because all network traffic should be untrusted, he said users must:
- verify and secure all resources,
- limit and strictly enforce access control, and
- inspect and log all network traffic.
That’s why zero trust is sometimes known by the motto, “Never Trust, Always Verify.”
How Do You Implement a Zero Trust Architecture?
As the definitions suggest, zero trust is not a single technique or product, but a set of principles for a modern security policy.
In its seminal 2020 report, the U.S. National Institute for Standards and Technology (NIST) detailed guidelines for implementing zero trust.
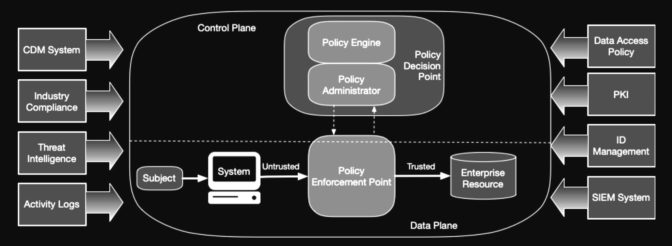
Its general approach is described in the chart above. It uses a security information and event management (SIEM) system to collect data and continuous diagnostics and mitigation (CDM) to analyze it and respond to insights and events it uncovers.
It’s an example of a security plan also called a zero trust architecture (ZTA) that creates a more secure network called a zero trust environment.
But one size doesn’t fit all in zero trust. There’s no “single deployment plan for ZTA [because each] enterprise will have unique use cases and data assets,” the NIST report said.
Five Steps to Zero Trust Security
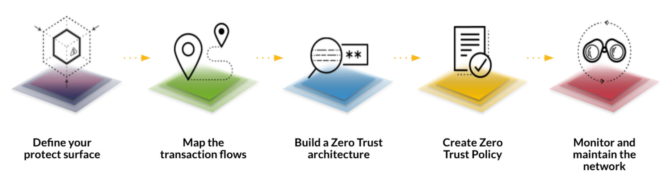
The job of deploying a zero trust architecture can be boiled down to five main steps.
It starts by defining a so-called protect surface, what users want to secure. That’s a departure from previous efforts in access management that focused on a so-called attack surface of specific vulnerabilities. A protect surface can span systems inside a company’s offices, the cloud and the edge.
Map a Zero Trust Architecture
From there, users create a map of the transactions that typically flow across their networks and a zero trust architecture to protect them.
Then they establish security policies for the network.
Finally, they monitor network traffic to make sure transactions stay within the policies across all workloads.
How Zero Trust Models Evolve
Both the NSTAC report (above) and Kindervag suggest these same steps to create a zero trust environment.
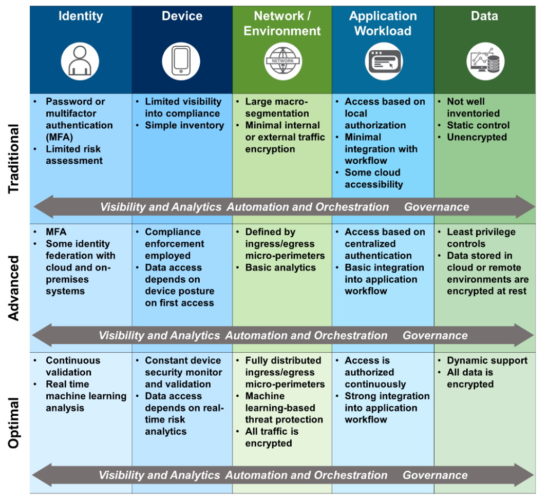
It’s important to note that zero trust is a journey not a destination. Consultants and government agencies recommend users adopt a zero trust maturity model to document an organization’s security improvements over time.
The Cybersecurity Infrastructure Security Agency, part of the U.S. Department of Homeland Security, described one such model (see chart below) in a 2021 document.
MFAs in Zero Trust Environments
In practice, users in zero trust environments request access to each protected resource separately. They typically use multi-factor authentication (MFA) such as providing a password on a computer, then a code sent to a smartphone.
It’s an access policy better suited to protecting sensitive data, apps and user identity as well as preventing malware and ransomware attacks.
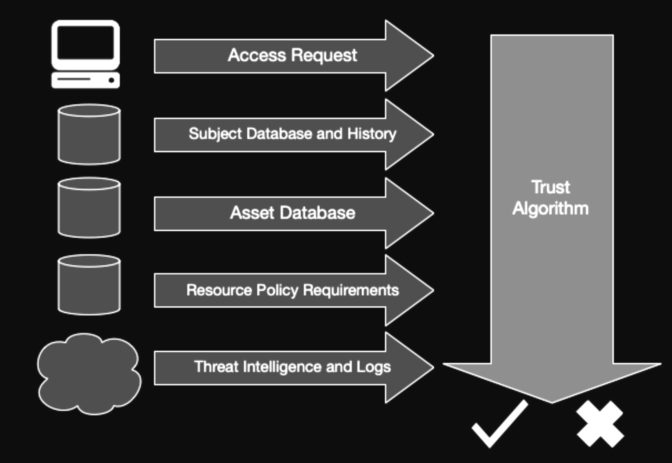
The NIST report lists ingredients for an algorithm (below) that determines whether or not a user gets access to a resource.
“Ideally, a trust algorithm should be contextual, but this may not always be possible,” given a company’s resources, it said.
Some argue the quest for an algorithm to measure trustworthiness is counter to the philosophy of zero trust policy. Others note that machine learning has much to offer here, capturing context across many events on a network to help make sound decisions on access.
The Big Bang of Zero Trust
In May 2021, President Joe Biden released an executive order mandating zero trust for the government’s computing systems.
The order gave federal agencies 60 days to adopt zero trust architectures based on the NIST recommendations. It also called for a playbook on dealing with security breaches, a safety board to review major incidents — even a program to establish cybersecurity warning labels for some consumer products.
It was a big bang moment for zero trust that’s still echoing around the globe.
“The likely effect this had on advancing zero trust conversations within boardrooms and among information security teams cannot be overstated,” the NSTAC report said.
What’s the History of Zero Trust?
Around 2003, ideas that led to zero trust started bubbling up inside the U.S. Department of Defense, leading to a 2007 report. About the same time, an informal group of industry security experts called the Jericho Forum coined the term “de-perimeterisation.”
Kindervag crystalized the concept and gave it a name in his bombshell September 2010 report.
The industry’s focus on building a moat around organizations with firewalls, VPNs and intrusion detection systems was wrongheaded, he argued. Bad actors and inscrutable data packets were already inside organizations, threats that demanded a radically new approach.
How Zero Trust Goes Beyond Firewalls
From his early days installing firewalls, “I realized our trust model was a problem,” he said in an interview. “We took a human concept into the digital world, and it was just silly.”
At Forrester, he was tasked with finding out why cybersecurity wasn’t working. In 2008, he started using the term zero trust in talks describing his research.
Zero Trust Microsegmentation
Instead of erecting a single network perimeter enforced by user access policies and permissions, he advocated a novel approach to network security based on least privileged access policies. Each endpoint should apply more granular access policies in a kind of network segmentation sometimes called microsegmentation.
After some early resistance, users started embracing the concept.
“Someone once told me zero trust would become my entire job. I didn’t believe him, but he was right,” said Kindervag, who, in various industry roles, has helped hundreds of organizations build zero trust environments.
What’s a Zero Trust Network Architecture
Indeed, Gartner projects that by 2025 at least 70% of new remote access deployments will use what it calls zero trust network access (ZTNA), up from less than 10% at the end of 2021. (Gartner, Emerging Technologies: Adoption Growth Insights for Zero Trust Network Access, G00764424, April 2022)
That’s in part because the COVID lockdown accelerated corporate plans to boost security for remote workers. And many firewall vendors now include ZTNA capabilities in their products.
Market watchers estimate at least 50 vendors from Appgate to Zscaler now offer security products aligned with the zero trust approach.
How AI Automates Zero Trust
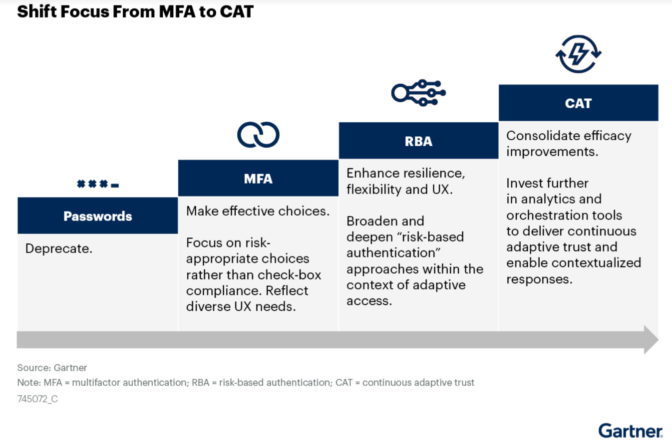
Users in some zero trust environments express frustration with repeated requests for multi-factor authentication. It’s a challenge that some experts see as an opportunity for automation with machine learning.
For example, Gartner suggests applying analytics in a security strategy it calls continuous adaptive trust. CAT (see chart below) can use contextual data — such as device identity, network identity and geolocation — as a kind of digital reality check to help authenticate users.
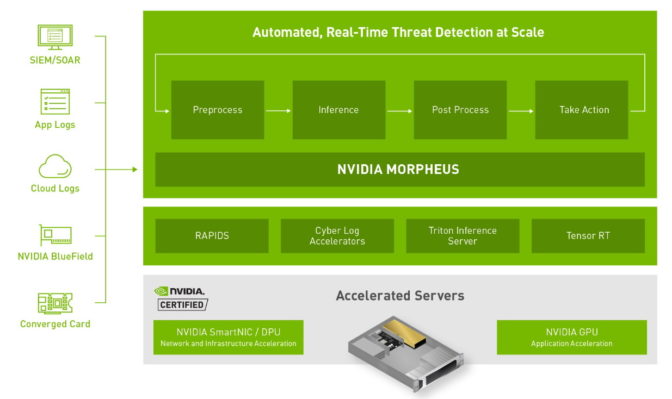
In fact, networks are full of data that AI can sift in real time to automatically weigh access requests and enhance security.
“We do not collect, maintain and observe even half the network data we could, but there’s intelligence in that data that will form a holistic picture of a network’s security,” said Bartley Richardson, senior manager of AI infrastructure and cybersecurity engineering at NVIDIA.
AI in Zero Trust Environments
Human operators can’t track all the sensitive data a network spawns or set policies for all possible vulnerabilities. But they can apply AI to scour data for suspicious activity, then respond fast.
“We want to give companies the tools to build and automate robust zero trust environments with defenses that live throughout the fabric of their data centers,” said Richardson, who leads development on NVIDIA Morpheus, an open AI cybersecurity framework and co-authored a technical blog on zero trust.
NVIDIA provides pretrained AI models for Morpheus, or users can choose a model from a third party or build one themselves.
“The backend engineering and pipeline work is hard, but we have expertise in that, and we can architect it for you,” he said.
It’s the kind of capability experts like Kindervag see as part of the future for a zero trust strategy.
“Manual response by security analysts is too difficult and ineffective,” he wrote in a 2014 report. “The maturity of systems is such that a valuable and reliable level of automation is now achievable.”
More Resources on Zero Trust
To learn more about AI and zero trust principles, read this blog or watch the video below. To learn more about how NVIDIA’s DPUs enable zero trust, read this technical blog.
Learn more about cybersecurity on the NVIDIA Technical Blog.